Featured
Table of Contents
Ipsec And Ike
IPsec verifies and secures data packets sent out over both IPv4- and IPv6-based networks. IPsec procedure headers are discovered in the IP header of a packet and define how the information in a packet is managed, including its routing and shipment throughout a network. IPsec includes several elements to the IP header, consisting of security info and one or more cryptographic algorithms.
ISAKMP is specified as part of the IKE procedure and RFC 7296. It is a framework for key establishment, authentication and negotiation of an SA for a safe and secure exchange of packets at the IP layer. Simply put, ISAKMP specifies the security specifications for how two systems, or hosts, communicate with each other.
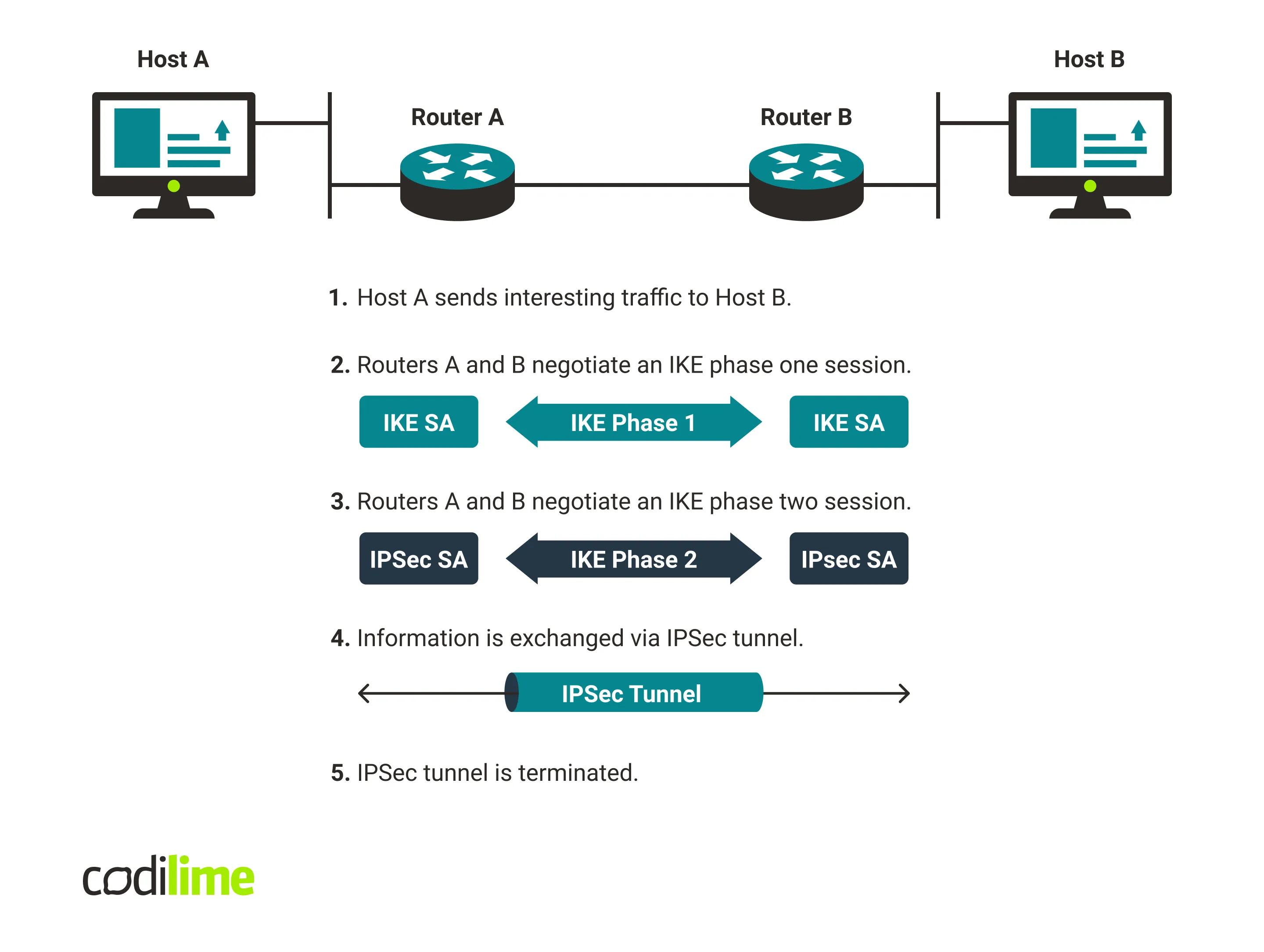
They are as follows: The IPsec process begins when a host system recognizes that a package needs defense and should be transmitted using IPsec policies. Such packages are considered "fascinating traffic" for IPsec functions, and they trigger the security policies. For outbound packets, this suggests the proper file encryption and authentication are applied.
About Virtual Private Network (Ipsec) - Techdocs
In the second step, the hosts utilize IPsec to work out the set of policies they will utilize for a secured circuit. They also verify themselves to each other and established a secure channel between them that is utilized to work out the way the IPsec circuit will secure or validate data sent out across it.

After termination, the hosts get rid of the private keys used throughout information transmission. A VPN essentially is a personal network executed over a public network. Anybody who connects to the VPN can access this personal network as if straight linked to it. VPNs are typically used in businesses to make it possible for staff members to access their corporate network from another location.
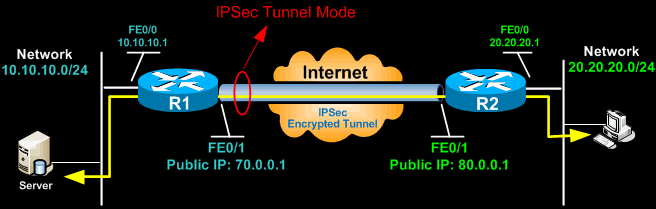
Usually used between safe network entrances, IPsec tunnel mode enables hosts behind one of the gateways to communicate firmly with hosts behind the other entrance. For example, any users of systems in a business branch office can safely link with any systems in the main office if the branch workplace and main office have secure entrances to function as IPsec proxies for hosts within the particular workplaces.
What Is Ipsec?
IPsec transport mode is used in cases where one host requires to interact with another host. The 2 hosts negotiate the IPsec circuit directly with each other, and the circuit is generally torn down after the session is total.
With an IPsec VPN, IP packets are secured as they take a trip to and from the IPsec gateway at the edge of a private network and remote hosts and networks. An SSL VPN protects traffic as it moves between remote users and an SSL entrance. IPsec VPNs support all IP-based applications, while SSL VPNs only support browser-based applications, though they can support other applications with customized development.
See what is best for your company and where one type works best over the other.
- Overview Of Ipsec -
Each IPsec endpoint verifies the identity of the other endpoint it desires to interact with, ensuring that network traffic and information are only sent to the intended and allowed endpoint. In spite of its terrific energy, IPsec has a few issues worth discussing. First, direct end-to-end interaction (i. e., transmission approach) is not always readily available.
The adoption of different regional security guidelines in large-scale dispersed systems or inter-domain settings might posture extreme problems for end-to-end interaction. In this example, assume that FW1 requires to check traffic content to detect intrusions which a policy is set at FW1 to reject all encrypted traffic so regarding implement its content evaluation requirements.
Users who utilize VPNs to from another location access a private business network are placed on the network itself, providing the very same rights and functional capabilities as a user who is linking from within that network. An IPsec-based VPN might be produced in a variety of ways, depending upon the needs of the user.
Site To Site Ipsec Vpn Phase-1 And Phase-2 Troubleshooting ...
Because these parts may originate from various providers, interoperability is a must. IPsec VPNs enable smooth access to business network resources, and users do not always require to use web access (gain access to can be non-web); it is therefore an option for applications that require to automate interaction in both methods.
Its framework can support today's cryptographic algorithms in addition to more effective algorithms as they appear in the future. IPsec is a compulsory part of Web Procedure Variation 6 (IPv6), which business are actively releasing within their networks, and is strongly suggested for Web Procedure Version 4 (IPv4) executions.
It supplies a transparent end-to-end protected channel for upper-layer protocols, and executions do not need modifications to those protocols or to applications. While possessing some downsides connected to its complexity, it is a fully grown procedure suite that supports a variety of file encryption and hashing algorithms and is extremely scalable and interoperable.
Ipsec
Like VPNs, there are lots of ways a No Trust design can be executed, however solutions like Twingate make the procedure significantly simpler than needing to wrangle an IPsec VPN. Contact Twingate today to read more.
IPsec isn't the most common internet security procedure you'll use today, but it still has an important role to play in protecting web communications. If you're using IPsec today, it's most likely in the context of a virtual personal network, or VPN. As its name suggests, a VPN creates a network connection between 2 machines over the general public web that's as protected (or nearly as protected) as a connection within a private internal network: most likely a VPN's a lot of well-known usage case is to allow remote staff members to access protected files behind a corporate firewall program as if they were working in the workplace.
For the majority of this post, when we say VPN, we mean an IPsec VPN, and over the next several sections, we'll describe how they work. A note on: If you're seeking to establish your firewall to permit an IPsec VPN connection, make certain to open UDP port 500 and IP ports 50 and 51.
Define Ipsec Crypto Profiles

As soon as this has all been set, the transportation layer hands off the information to the network layer, which is mainly controlled by code running on the routers and other elements that comprise a network. These routers pick the route specific network packages require to their location, but the transport layer code at either end of the communication chain does not need to know those information.
On its own, IP doesn't have any built-in security, which, as we noted, is why IPsec was developed. Today, TLS is developed into practically all internet browsers and other internet-connected applications, and is more than adequate defense for everyday web usage.
That's why an IPsec VPN can add another layer of defense: it involves protecting the packets themselves. An IPsec VPN connection begins with facility of a Security Association (SA) in between two interacting computer systems, or hosts. In general, this involves the exchange of cryptographic keys that will permit the celebrations to secure and decrypt their interaction.
Latest Posts
The 6 Best Vpn Stocks To Buy Right Now For August 2023
The Top 10 Enterprise Vpn Solutions
Best Vpn Service 2023: Vpns Tested By Our Experts