Featured
Table of Contents
What Is An Ipsec Vpn?
For a complete technical description of IPsec works, we suggest the outstanding breakdown on Network, Lessons. There are that figure out how IPsec customizes IP packages: Internet Secret Exchange (IKE) establishes the SA in between the communicating hosts, working out the cryptographic keys and algorithms that will be used in the course of the session.
The host that receives the package can utilize this hash to make sure that the payload hasn't been modified in transit. Encapsulating Security Payload (ESP) encrypts the payload. It also includes a sequence number to the package header so that the getting host can be sure it isn't getting replicate packets.
At any rate, both procedures are constructed into IP applications. The encryption established by IKE and ESP does much of the work we expect out of an IPsec VPN. You'll observe that we've been a little vague about how the encryption works here; that's because IKE and IPsec allow a large range of file encryption suites and technologies to be utilized, which is why IPsec has handled to survive over more than twenty years of advances in this location.

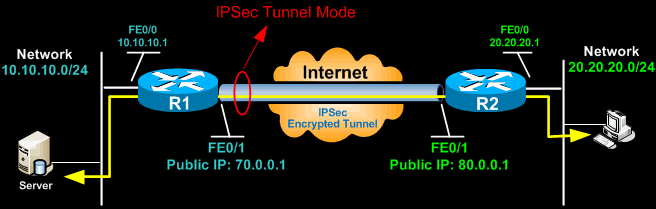
There are two various methods in which IPsec can operate, referred to as modes: Tunnel Mode and Transportation Mode. The difference between the 2 pertains to how IPsec deals with package headers. In Transportation Mode, IPsec encrypts (or authenticates, if only AH is being used) only the payload of the packet, but leaves the existing package header data more or less as is.
Ipsec Vpn Overview
When would you use the different modes? If a network packet has been sent from or is predestined for a host on a personal network, that package's header consists of routing information about those networksand hackers can examine that information and utilize it for wicked functions. Tunnel Mode, which secures that details, is usually used for connections in between the gateways that sit at the outer edges of personal business networks.
Once it comes to the entrance, it's decrypted and removed from the encapsulating package, and sent out along its way to the target host on the internal network. The header information about the topography of the personal networks is therefore never ever exposed while the packet passes through the public internet. Transportation mode, on the other hand, is typically used for workstation-to-gateway and direct host-to-host connections.
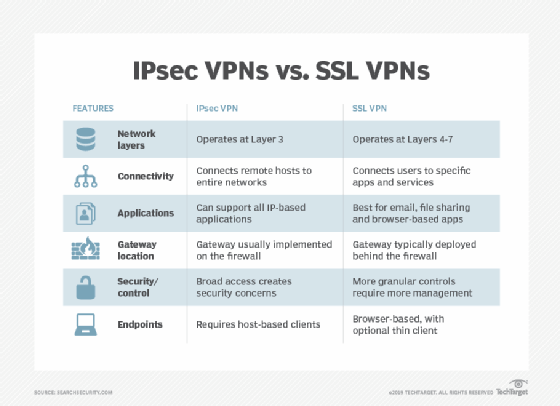
On the other hand, because it uses TLS, an SSL VPN is protected at the transportation layer, not the network layer, so that might affect your view of how much it boosts the security of your connection. Where to read more: Copyright 2021 IDG Communications, Inc.
In short, an IPsec VPN (Virtual Private Network) is a VPN running on the IPsec protocol. In this article, we'll describe what IPsec, IPsec tunneling, and IPsec VPNs are.
Internet Protocol Security Explained
IPsec stands for Web Protocol Security. In other words, IPsec is a group of protocols that set up a secure and encrypted connection in between devices over the public web.
Each of those three separate groups takes care of separate special jobs. Security Authentication Header (AH) it makes sure that all the data originates from the exact same origin and that hackers aren't attempting to pass off their own littles information as legitimate. Imagine you get an envelope with a seal.
This is but one of two methods IPsec can run. The other is ESP. Encapsulating Security Payload (ESP) it's a file encryption protocol, implying that the data plan is transformed into an unreadable mess. Aside from file encryption, ESP resembles Authentication Headers it can verify the information and inspect its stability.
On your end, the encryption happens on the VPN client, while the VPN server takes care of it on the other. Security Association (SA) is a set of specs that are concurred upon in between 2 devices that develop an IPsec connection. The Internet Key Exchange (IKE) or the essential management protocol becomes part of those specifications.
What Is Ipsec? Definition & Deep Dive
IPsec Transport Mode: this mode encrypts the information you're sending but not the info on where it's going. So while malicious actors couldn't read your intercepted interactions, they could tell when and where they were sent. IPsec Tunnel Mode: tunneling develops a safe, enclosed connection between two devices by using the usual internet.
A VPN using an IPsec procedure suite is called an IPsec VPN. Let's state you have an IPsec VPN client running. You click Link; An IPsec connection starts utilizing ESP and Tunnel Mode; The SA develops the security parameters, like the kind of encryption that'll be utilized; Data is prepared to be sent and gotten while encrypted.
MSS, or optimum section size, describes a worth of the maximum size a data package can be (which is 1460 bytes). MTU, the optimum transmission system, on the other hand, is the worth of the optimum size any gadget connected to the internet can accept (which is 1500 bytes).
And if you're not a Surfshark user, why not turn into one? We have more than just IPsec to offer you! Your personal privacy is your own with Surfshark More than simply a VPN (Internet Key Exchange version 2) is a procedure used in the Security Association part of the IPsec protocol suite.
What Is Ip Security (Ipsec), Tacacs And Aaa ...
Cybersecurity Ventures anticipates international cybercrime costs to grow by 15 percent per year over the next 5 years, reaching $10. 5 trillion USD every year by 2025, up from $3 trillion USD in 2015. And, cyber attacks are not restricted to the private sector - federal government companies have suffered significant data breaches.

Some might have IT programs that are out-of-date or in requirement of security patches. And still others just may not have an adequately robust IT security program to safeguard against increasingly advanced cyber attacks. Thinking about these elements, it is easy to see why third-party suppliers are a prime target for cybercrime.
As displayed in the illustration below, Go, Silent protects the connection to business networks in an IPSec tunnel within the enterprise firewall program. This allows for a fully protected connection so that users can access business programs, objectives, and resources and send, shop and obtain information behind the safeguarded firewall without the possibility of the connection being intercepted or pirated.
Web Procedure Security (IPSec) is a suite of protocols normally utilized by VPNs to develop a protected connection over the internet. IPSec is usually carried out on the IP layer of a network.
Latest Posts
The 6 Best Vpn Stocks To Buy Right Now For August 2023
The Top 10 Enterprise Vpn Solutions
Best Vpn Service 2023: Vpns Tested By Our Experts